jay's some development note
linux
driver
- ramfs、initrd
display
tools
others
jay's some development note
linux
driver
display
tools
others
浏览器被污,所有主页均设置为2345.com,日狗,按照网上方法依次尝试,无果。自己着手解决。
怀疑是有一个守护进程,以上更改生效后立即被重新更改,导致无效。尝试在任务管理器->性能->资源监视器->CPU 选项卡中搜索2345,出现以下句柄。
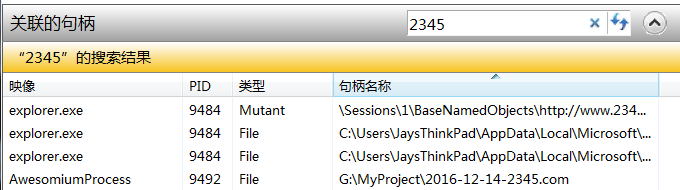
映像 PID 类型 句柄名称
explorer.exe 9484 Mutant \Sessions\1\BaseNamedObjects\http://www.2345.com/
explorer.exe 9484 File C:\Users\JaysThinkPad\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I4IR8LS1\2345_160926[1].eot
explorer.exe 9484 File C:\Users\JaysThinkPad\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\VFB0GG7W\2345_com[1].htm不难看出这里主要是资源管理器相关,怀疑是有程序直接注入了explorer.exe,尝试删除以上关联句柄的注册表和本地文件。但是在启动浏览器时候又马上被生成。
我们尝试按照一线方法结束资源管理器进程的这些Mutex。
Kill mutex (mutant) of an other process
下载handle.exe
Microsoft Windows [版本 6.1.7601]
版权所有 (c) 2009 Microsoft Corporation。保留所有权利。
C:\Users\JaysThinkPad>cd /d H:\Program Files\Handle
H:\Program Files\Handle>handle64.exe -p 9300 -a 2345H:\Program Files\Handle>handle64.exe -p 1480 -a 2345
Nthandle v4.1 - Handle viewer
Copyright (C) 1997-2016 Mark Russinovich
Sysinternals - www.sysinternals.com
explorer.exe pid: 1480 type: File F88: C:\Users\JaysThinkPad\A
ppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I4IR8LS1\234
5_160926[1].eot
explorer.exe pid: 1480 type: Mutant FA8: \Sessions\1\BaseNamedOb
jects\http://www.2345.com/
explorer.exe pid: 1480 type: File 1228: C:\Users\JaysThinkPad\A
ppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\UN36B2RC\234
5_com[1].htm
explorer.exe pid: 1480 type: File 16EC: G:\MyProject\2016-12-14
-2345.com
explorer.exe pid: 1480 type: File 16F4: G:\MyProject\2016-12-14
-2345.com>handle64.exe -p 9300 -c F88按照以上方法结束了所有的2345句柄,同时尝试删除注册表和本地文件,问题依然。
但是这里发现一个问题,就是explorer中的句柄并不是一直存在的,是启动浏览器后被主动注入的。
但是启动搜狗浏览器的时候却没有改句柄,说明是浏览器程序本身被污染了。
同时不难看出IE浏览器也是同样的方式被注入了句柄。
映像 PID 类型 句柄名称
iexplore.exe 4744 File C:\Users\JaysThinkPad\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I4IR8LS1\2345_160926[1].eot
iexplore.exe 4744 File C:\Users\JaysThinkPad\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\UN36B2RC\2345_com[1].htm
iexplore.exe 4744 Mutant \Sessions\1\BaseNamedObjects\http://www.2345.com/Pushing the Limits of Windows: Handles
The kernel-mode core of Windows, which is implemented in the %SystemRoot%\System32\Ntoskrnl.exe image, consists of various subsystems such as the Memory Manager, Process Manager, I/O Manager, Configuration Manager (registry), which are all parts of the Executive. Each of these subsystems defines one or more types with the Object Manager to represent the resources they expose to applications. For example, the Configuration Manager defines the key object to represent an open registry key; the memory manager defines the Section object for shared memory; the Executive defines Semaphore, Mutant (the internal name for a mutex), and Event synchronization objects (these objects wrap fundamental data structures defined by the operating system’s Kernel subsystem); the I/O Manager defines the File object to represent open instances of device driver resources, which include file system files; and the Process Manager the creates Thread and Process objects I discussed in my last Pushing the Limits post. Every release of Windows introduces new object types with Windows 7 defining a total of 42. You can see the objects defined by running the Sysinternals Winobj utility with administrative rights and navigating to the ObjectTypes directory in the Object Manager namespace:
H:\Program Files\volatility_2.4.win.standalone>volatility-2.4.standalone.exe -f memory_images/example.vmem --profie=Win7SP1x64 handles -p 3488 -t Mutant -s
H:\Program Files\volatility_2.4.win.standalone>volatility-2.4.standalone.exe -f memory_images/example.vmem imageinfo
H:\Program Files\volatility_2.4.win.standalone>volatility-2.4.standalone.exe -f memory_images/example.vmem --profie=Win7SP1x64 pslist
H:\Program Files\volatility_2.4.win.standalone>volatility-2.4.standalone.exe -f memory_images/example.vmem --profie=Win7SP1x64 vaddump -p 1752 -D memory_images/procdump/12/17/2016 3:47:47 PM
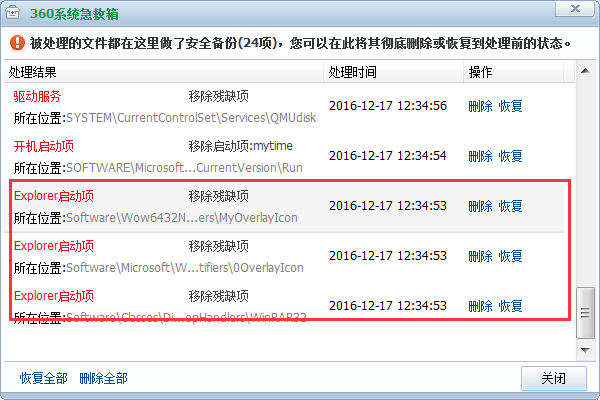
最后还是通过360系统急救箱扫描解决问题,有些异常可能和2345.com有关系。安装过程发现根本没有办法安装系统急救箱工具,因为在不能在 资源管理器中新建 “SuperKiller.exe”,怀疑其和Explorer启动项有关系。将360压缩包中的SuperKiller.exe 重命名后解压正常。